Tor’s Attack and its Impact on Piracy
 It’s been a busy weekend for the Tor community as one of its most prominent members has been arrested and, perhaps more importantly, by at least one estimate, half of all Tor sites have been shuttered and/or compromised.
It’s been a busy weekend for the Tor community as one of its most prominent members has been arrested and, perhaps more importantly, by at least one estimate, half of all Tor sites have been shuttered and/or compromised.
Tor, which stands for The Onion Router, is a combination of free software and an open, decentralized network that is designed around anonymity and privacy.
However, as one would imagine any network built around privacy would be, it’s uses have been mixed. Though some have used it for legitimate purposes, many have turned to it for illegal activities including copyright infringement, buying/selling illegal goods and services and even child pornography.
While the recents security breaches haven’t shuttered the Tor network or even some of its most notorious sites, it’s definitely impacted the way people think about Tor. Though the truly savvy always knew something like this was possible but many of those turning to Tor were not fully aware of the risks.
So what does this mean for Tor and some of the less than desirable activities that take place on it? Let’s take a look at what happened and find out.
The Basics of Tor
 To understand what happened over the weekend, we have to fist understand at least the basics of what Tor is and how it works.
To understand what happened over the weekend, we have to fist understand at least the basics of what Tor is and how it works.
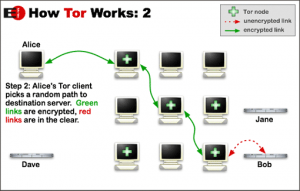
Tor is, at its core, a service to anonymize Internet traffic. It does this by passing Internet traffic through a series of intermediaries, also known as relays, as shown in the image to the right from the Electronic Frontier Foundation.
All traffic inside the Tor network is encrypted and, since each relay only sees what came before it and where it’s going (one “hop” in the path) it can’t tell what traffic it’s passing on or where it is going to. Only the exit relay, which presents the unencrpyted traffic to the actual destination, can see the content but it can not connect the data with the originator.
This method of routing traffic is used to enable Tor users to visit sites anonymously, never exposing their original IP address. Since each path is only temporary, it’s impossible to trace back to the source after the fact.
The other side of the coin are hidden sites and hidden services, which use the same technique to provide content and services solely to those who are using the Tor network. These have included services such as Tormail, an email service for Tor users, but also sites like Silk Road, which is a marketplace specializing in the buying and selling of illegal goods and services.
It was those hidden services that were compromised and taken down, removing a large chunk of the Tor network and, possibly, compromising the computers of a large number of Tor users.
What Happened to Tor
Much of what happened over the weekend is still up for debate but here is a roundup of what is known.
First, on Friday, Eric Eoin Marques from Dublin, Ireland was arrested. The arrest was prompted by a warrant from the U.S. that accused him of being “the largest facilitator of child porn on the planet.”
Morquest is alleged to be behind a company known as Freedom Hosting, which is one of the largest hosting providers that sets up hidden services. (Note: Freedom Hosting does not have a connection to the Tor Project itself.)
Freedom Hosting itself was also compromised during this time. The servers were configured in such a way that visitors were directed to a “Down for maintenance” message but the page contained a JavaScript exploit, one that attempted to install Malware on the user’s system, which then sent the IP address of the user to a computer located in Virginia.
Though it’s not known who compromised the servers, many suspect the U.S. government due to the timing of the attack and the use of a Virginia IP address. This has spread fears that Silk Road, which was not affected, could be next and that its closure could have dramatic impacts outside of the Tor network, in particular with the Bitcoin currency.
Regardless though, the immediate impact is clear. A large number of Tor-based sites are down and many of Tor’s users are possibly compromised. Though Tor will probably recover from this, it’s image of invulnerability likely won’t.
The Impact for Copyright Holders (and Others)
To be honest, the Tor network has never really been a hotbed for copyright infringement. The Tor network simply has too many problems to be a go-to destination for pirated content.
For one, it’s much more complex than most other available solutions, it’s much slower due to the use of multiple intermediaries and copyright infringement, though illegal, is seen as a relatively “safe” activity to do on the unprotected Internet because it is so common. Most of those who want to infringe content privately simply use a virtual private network (VPN) rather than go through Tor.
Still, some content was frequently traded on Tor including material that might be illegal in one’s home country (even if it was legal where it was produced) and content that would be seen as embarrassing. This has included many genres of pornography, banned movies and even literature.
But even with that in mind, the Tor audience is still fairly small, with only a limited number of people using Tor to access infringing material.
However, there was a real fear that Tor, and networks like it, could represent the future of piracy. As latency and complexity issues are lessened and legal attacks on traditional pirate sites grew, it was feared that more and more infringers could turn to Tor to get their illegal goods.
Today though, that appears less likely. Not only because piracy is still going strong on the traditional Web, but because the veneer of invulnerability in Tor has been cracked. Though it wasn’t Tor itself that was cracked, instead it appears to be other software used to run the servers, the idea of the Tor network being “bulletproof” is gone.
Bottom Line
In reality, Tor was never really the future of piracy. Piracy is a much more casual crime than most of what Tor is known for. People who pirate content, typically don’t fear getting caught. Even the use of VPNs to hide one’s activities is still low.
Instead, piracy is, in many ways, a crime of convenience. Most people pirate because they want something for free, they want it now and don’t care how they get it. Tor, however, is definitely not convenient. It’s slower and more difficult. With easier alternatives out there, Tor is not going to be a likely destination for pirates, except in some extreme cases.
So the recent attack on Tor doesn’t, most likely, have a major impact for content creators. Instead, the biggest change is the perception of safe havens existing online has taken a huge blow. After all, if it was a government attack, they breached one of the most supposedly secure places on the Web.
This puts the security of other services, such as private BitTorrent trackers, into check.
Want to Reuse or Republish this Content?
If you want to feature this article in your site, classroom or elsewhere, just let us know! We usually grant permission within 24 hours.