Ad Injection: A Worry for Webmasters Too
 An article yesterday by Nate Anderson on Ars Technica tells a very worrisome tale.
An article yesterday by Nate Anderson on Ars Technica tells a very worrisome tale.
According to the story, Robert Silvie visited his parents home and, when using their Internet access, noticed a series of banner ads that should not have have been there. After eliminating other causes, such as malware and a compromised router, Silvie realized that the Ads were being put there by his parents’ ISP, CMA Communications.
Others have confirmed this, though it doesn’t appear that all CMA Communications customers are affected yet, and a recent change to CMA Communications’ terms of service seems to drive the point home.
To make a long story short, CMA Communications has partnered with R66T, pronounced “Root 66”, to deliver ads to their customers. Those ads are either inserted into the web pages directly or appear as banner overlays at the bottom of the page.
But while CMA Communications customers are understandably upset about this, considering that they are viewing the ads in addition to paying for the Internet access, webmasters and other authors have cause to get upset as well.
This move doesn’t just impact customers of CMA Communications, but anyone who publishes a website, large or small. Furthermore, while it is currently limited to one relatively small ISP, if others were to take it up, it could spell disaster for many webmasters, sabotaging both their sites and their business models.
This is a problem that needs to be nipped in the bud, before the Web at large starts to suffer for it.
How it Works
 The basic principle behind this kind of embedding is actually fairly simple. Once your traffic leaves your router and is on your ISP’s network, it is completely out of your control and it’s up to the ISP (and other networks) to make sure that it’s routed to the correct place.
The basic principle behind this kind of embedding is actually fairly simple. Once your traffic leaves your router and is on your ISP’s network, it is completely out of your control and it’s up to the ISP (and other networks) to make sure that it’s routed to the correct place.
Typically, ISPs do this reasonably well. However, CMA Communications has decided that it will route non-secured traffic through R66T’s servers. As the traffic passes through those servers, the data in the page is analyzed and ads are inserted, either inline with the page (often over other ads) or as an overlay at the bottom of is a suitable place can’t be found.
There’s very little that a non-tech-savvy user can do to stop this. Users don’t control the traffic at the point the redirection happens and, given that ISPs have very limited competition (in particular in CMA Communications, which operates mostly in rural areas), this makes leaving the ISP almost impossible.
This means that customers are held hostage by this redirection and webmasters have very limited say in it eitherl. After all, if your site is visited by someone on CMA Communications, those ads are placed whether you want them or not.
This is all done by someone who is supposed to be an intermediary and that should make webmasters very, very mad.
Why Webmasters Should Worry
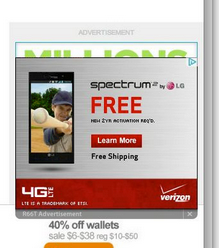 The problem with this from a webmaster is simple is simple: CMA Communications and R66T are modifying your site without your permission and doing it, specifically, to place new advertisements on your work.
The problem with this from a webmaster is simple is simple: CMA Communications and R66T are modifying your site without your permission and doing it, specifically, to place new advertisements on your work.
Not only is this an unwanted monetization of your content by a third party, it doesn’t benefit you in any way. There’s no cut of the advertising money coming to you, no additional traffic to be gained and no promotion of your site at all.
Worse still, the effort harms your site by displaying ads that you don’t want on it, most egregiously, even covering up existing ads on your site (if you have any). This means that visitors can’t click your ads and, even if they can, the added advertisements mean that they are less likely to click yours.
But even if your site doesn’t run advertisements, as with Plagiarism Today, it was likely a business or a personal decision that’s damaged by the move. For me, I chose to not run ads because I wanted Plagiarism Today to be a free service, one that I’m able to support through my consulting practice.
That’s the way it has been for years and the way I’d like to keep it. I’m not happy that CMA Communications and R66T have decided, without my input, that I can’t keep it that way for everyone.
Is This Legal?
All of this raises an interesting question: Is modifying your site like this legal?
That’s a tough question to answer as the issues around this insertion are nowhere near settled.
As we discussed in 2005, there are a lot of legal questions about the issue of Framing, issues that still aren’t resolved today. However, the DiggBar controversy of 2009 showed how much of a hot button issue it still can be.
More recently, Lightbox linking, linking in a popup overlay, also saw some controversy but there were no legal cases to address the issue.
However, what R66T and CMA Communications are doing goes well beyond mere framing, which many associate with being simply another form of linking, and actually manipulates the HTML code of the page as it is being transmitted. This raises a pair of very serious concerns legally:
- Copyright Law: The manipulation of the source code could be seen as creating a derivative work based upon the original site, a possible infringement under the law.
- Trademark Law: A company, like Apple, could claim that the injection of R66T’s ads into their site implies a relationship between the companies that does not exist and causes confusion in the marketplace.
However, neither of these legal arguments are really guaranteed to work. This area of the law is really just to unsettled and both CMA Communications and R66T will be quick to point out that end users manipulate sites all the time through Adblocking scripts and other tools.
To counter, one would likely argue that those are decisions made by the end user with their browser and they usually don’t do so for financial gain. But then arguments could be raised about services like Opera Turbo, which acts as a proxy to compress images and other Web content for faster download on slow or data-limited connections.
It’s clear that there are a lot of unanswered questions here but it seems to me, at the very least, that CMA Communications and R66T are, at the very least, stepping into a legal gray area when it comes to site manipulation.
What Can Be Done to Stop It
Though litigation may eventually be a tool to prevent this, in the short term webmasters and consumers that want to avoid these injected ads have at least a few ways to do so but they all center around the weakest link in the system, the fact it does not work with secure web pages or connections.
If you’re a CMA Communications user and are having these ads forced upon you, the simplest solution is to use a virtual private network (VPN) that gives you a secure connection to an outside server to pass your data through.
Basically, what this does is create a secure “tunnel” between your computer and a remote one, a tunnel that R66T can not snoop on or modify, letting you access sites without ads. Though it may slow your connection down some, it’s likely less of a hassle than being bombarded by additional unwanted ads.
If you’re a webmaster, you may have the option of forcing visitors to use the secure version of your page. This will not work on all sites, in particular those where you don’t control the server, but has the same impact.
Be warned though, such a move will create additional strain on your server and may slow down access somewhat, but the difference, for most, is minimal.
In the end, this debacle may be a lesson in the importance of a secure Internet, not to protect ourselves against hackers and thieves, but against bad-acting ISPs.
Bottom Line
To be clear, we have seen this kind of site manipulation before. R66T is best known for running free hotspots that are paid for through bars and overlays that show advertisements.
However, this is the first time that we’ve seen this kind of technology used on a paid for Internet account. Where the ads on free hotspots were payment for use of a secondary form of Internet access, this CMA Communications is using the technology on a primary and subscriber-funded system. This not only greatly increases the annoyance for users, but also the concern for webmasters.
As content creators, we are entrusting ISPs to carry our work to the people that want to access it faithfully. CMA Communications and R66T have broken that trust.
This is one time that both webmasters and users should be united in taking a stand against a company’s practices. What CMA Communications has done is solely in its best interest and does nothing to service its customers or the people whose work travels along their network.
It was a selfish decision that needs to be treated with appropriate scorn before others decided to follow suit.
Want to Reuse or Republish this Content?
If you want to feature this article in your site, classroom or elsewhere, just let us know! We usually grant permission within 24 hours.
